Цікаве спостереження - погляд ззовні на протести..
- 03.08.23, 13:04

Пользуясь HSoft KeYs Вам не нужно будет тратить много времени на поиски нужных ключей для антивируса или другой программы. Программа имеет русскоязычный интуитивно понятный и простой в использовании интерфейс. Поддерживает: - avast! - Avira - Cracks - Dr. Web - ESET NOD32/Smart Security - Kaspersky Internet Security/Antivirus - KeyGens - Norton - USB - Русификаторы - Любой другой антивирус Скачать программу

Антивирусный сканер Hitman Pro предназначен для выявления и удаления различных шпионских и вредоносных программ с Вашего компьютера. Особенность сканера в том, что он использует базы сигнатур самых известных программ: Ad-Aware SE Personal, Spy Sweeper, Spybot Search & Destroy, CWShredder, SpywareBlaste, Spyware Block List, Sysclean Package, SuperDAT VirusScan. Сканер автоматически проверит наличие обновлений по всех базах и комплексно просканирует систему на предмет наличия шпионского ПО. Сканер не требует инсталляции и может работать с любого съемного носителя. Кроме всех возможностей присущих антивирусным сканерам подобного класса Hitman Pro имеет следующие отличительные особенности * Режимы работы: 1. Стандартный поиск; 2. Быстрый поиск; 3. Система раннего реагирования (обнаружение следов заражения системы). * Использование технологии Поведенческого сканирования - SurfRight сделал обширные исследования вредоносных файлов, чтобы определить общие характеристики (поведение) вредоносных программ. Сканер Hitman Pro использует эти исследования, когда он сканирует компьютер на наличие вирусов. * Подробная информация по каждому подозрительному файлу. * Поддержка ежедневного поиска инфекций во время запуска системы. * Короткое время сканирования - всего нескольких минут. * Поддержка автоматической загрузки подозрительных файлов для сканирования их в системе – Scan Cloud. Scan Cloud представляет собой кластер из нескольких компьютеров, постоянно работающих в сети Интернет. Невозможность ложных срабатываний на важные системные файлы, благодаря профилированию и белому списку. * Автоматическое создание точки отката перед очисткой системы от инфекций. Скачать программу

Антивирусный сканер IObit Malware Fighter предназначен для удаления вредоносных программ с вашего компьютера. Сканер позволяет обнаружить, удалить и заблокировать нежелательные приложения. Продвинутый алгоритм поиска вредоносных программ (malware) и программ-шпионов (Spyware) обнаруживает и удаляет самые глубокие инфекции, защищая компьютер от различных угроз. Кроме всех возможностей характерных для сканеров данного класса IObit Malware Fighter имеет следующие отличительные особенности: * Уникальный "Dual-Core" движок, использование технологии на уровне драйвера и эвристическое обнаружение позволяет обнаруживать самые глубокие инфекции. * Три режима сканирования (Умное сканирование, Полное сканирование, Выборочное сканирование). * Поддержка защиты в реальном времени: 1. Процессов автозагрузки; 2. Текущих системных процессов; 3. Сети (от WEB страниц которые содержат потоки); 4. Запускаемых файлов; 5. Cookie; 6. Браузера; 7. Сменных носителей, подключаемых к USB-портам; 8. От проявления вредоносной активности. * Поддержка безопасности путем сканирования на основе облачных технологий. Полное название: IObit Malware Fighter 1.1 Portable Год выпуска: 2011 Оф.сайт: http://iobit.com Язык интерфейса: Английский Платформа: Windows 2K/XP/Vista/Windows 7
Скачать



Cлужит для того, чтобы содержать Ваш PC в оптимально работающем состоянии. Error Repair Pro очистит и восстановит ошибки в Вашем PC единственным щелчком мыши. Всего несколько несколькими легких шагами, Вы сможете просмотреть весь реестр. Удалит, и исправит ошибки для любых неправильных записей и обеспечит вывод списка найденных ошибок. Так же Вы можете выборочно (вручную) исправлять любую ошибку или автоматически восстанавливать после сбоя в работе. Keep your PC operating smoothly by using Error Repair Professional to scan, identify, clean and repair errors in your PC with a single click. With a few easy steps, it will scan your entire registry for any invalid entries and provides a list of the registry errors found. You can then choose to selectively clean each item or automatically repair them all. "95% of All PCs Have Hidden Errors on Them! Let Us Scan Your PC and Discover How Many Errors Are Lurking Inside It..." "Eliminate Them Instantly and Have The Peace Of Mind Knowing Your PC is Automatically Kept Error Free, 24 Hours A Day!" Информация о программе: Язык интерфейса: английский Год выхода: 2010 Размер (RAR): 2.27 Мб


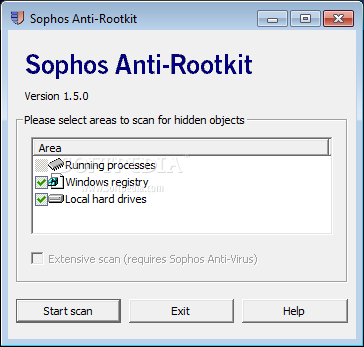
Утилита для обнаружения и удаления из системы вредоносных скрытых объектов (Rootkit). Программа Sophos Anti-Rootkit имеет удобный графический интерфейс, показывающий информацию о спрятанных системных ресурсах, включая имена всех распознанных руткитов и требуемые действия. Cпособна обнаруживать и удалять известные и неизвестные активные руткиты. В отличие от других имеющихся программ, утилита Sophos Anti-Rootkit выдает пользователю предупреждение в случае, если удаление какого-либо конкретного руткита повлияет на производительность или целостность операционной системы зараженного компьютера. Руткиты классифицируются как вредоносный софт, который может вызвать сбои в работе операционной системы. Их используют хакеры для быстрого и беспрепятственного доступа к компьютеру жертвы. Sophos Anti-Rootkit scans, detects and removes any rootkit that is hidden on your computer using advanced rootkit detection technology. Rootkits can lie hidden on computers and remain undetected by anti-virus software. Although new rootkits can be prevented from infecting the system, if you had any rootkits before you installed your anti-virus, they may never be revealed. Removing rootkits without compromising system integrity is particularly challenging and needs to be done with care. Simplified management Using Sophos Anti-Rootkit is easy. Whether you use its simple graphical user interface or run it from the command line, you can easily detect and remove any rootkits on your computer. Easy to use Sophos Anti-Rootkit provides an extra layer of protection, by safely and reliably detecting and removing any rootkit that might already have hidden itself on your system. Stay free of rootkits As part of its complete protection of endpoint computers, Sophos Endpoint Security and Data Protection has an integrated detection functionality that removes and prevents them being installed onto your desktops, laptops and servers. Информация о программе: Язык интерфейса: английский Разработчик: sophos.com Год выхода: 2010 Размер (RAR): 1.2 Мб Скачать программу


Spyware Terminator - программа для защиты компьютера от различных вредных модулей - spyware, adware, кейлоггеров и других троянов. Имеет резидентный монитор, который в реальном времени проводит мониторинг системы и предотвращает попытки проникновения на компьютер вредоносного ПО. Кроме этого, имеющийся в программе сканер поможет отыскать и поместить в "карантин" или удалить уже внедренные объекты. Работает программа очень быстро... Spyware Terminator имеет опцию автоматического обновления своих баз через Интернет, а также умеет производить проверку по расписанию. Основные характеристики Spyware Terminator: - Быстрое и полное сканирование. Spyware Terminator проверяет все важны части системы компьютера (процессы, библиотеки, панели инструментов, регистр, меню старт...). Возможность выбора области сканирования. - Автоматизация сканирования. Пользователь может запланировать время начала сканирования. - Отчеты Spyware Terminator. По окончании сканирования, пользователь может просмотреть детальную информацию о состоянии системы. - Интеграция антивируса. Spyware Terminator позволяет пользователю интегрировать бесплатный антивирус ClamAV. При этом проверка на наличие вредных программ происходит одновременно со сканированием на наличие шпионских программ. Обновление базы данных антивируса ClamAV происходит одновременно с обновлением Spyware Terminator. - Эффективное удаление найденных угроз. Подозрительные файлы перемещаются в специальный карантин и могут, если это необходимо, быть восстановлены. - Защита в режиме реального времени гарантирует то, что шпионские программы могут быть обнаружены и удалены до того как они будут установлены. - Spyware Terminator HIPS. HIPS защищает ваш компьютер от запуска подозрительных утилит, которые могут просочиться через дыры в безопасности системы или программного обеспечения. - Возможность уничтожения блокированных файлов. Spyware Terminator позволяет удалять некоторые файлы, которые нельзя удалить обычным путем. - Обновление. Возможность обновления как в автоматическом режиме, так и по желанию пользователя. Компактные файлы обновлений - скачиваются только измененные файлы. Возможность обновления только базы данных Spyware Terminator.



NirLauncher Package - набор из более 100 утилит для восстановления паролей, настройки, диагностики и мониторинга ОС семейства Windows, включая контроль сети, просмотр и извлечение cookies, кэш, хранившую Вашим Web-браузером, а также многие другие утилиты собранные в единый архив и объединённых в удобную оболочку. Интегрированы утилиты от NirSoft и Sysinternals. Особенности: * Утилиты портативны и могут запускаться с любого носителя информации, без инсталляции. * Все утилиты в пакетах - полностью свободно распространяемое обеспечение, без любого Spyware/Adware/Malware. * Пакеты включают разнообразие инструментальных средств, для своего ежедневного компьютерного использования, включая утилиты просмотра потерянных паролей, контроль сети, просмотр и извлечение cookies, кэш, и другую информацию. * Для каждой утилиты, Вы можете легко рассмотреть файл справки, или перейти к Web-странице. * В зависимости от разрядности системы автоматически запускаются утилиты для x86 или x64 систем. Список входящих утилит в NirLauncher Package 1.06.05: AlternateStreamView 1.12 Find all hidden alternate streams stored in the file system. AppCrashView 1.05 Displays the details of all application crashes occurred in your system. Asterisk Logger 1.04 Reveals the passwords stored behind the asterisks ('***') boxes AdapterWatch 1.05 displays useful information about your network adapters. ActiveXHelper 1.12 view essential information about ActiveX components installed on your computer. BlueScreenView 1.26 Show information about blue screen crashes occurred in your system. BluetoothCL 1.05 Show bluetooth devices list BluetoothView 1.36 Monitors the activity of Bluetooth devices around you. BulkFileChanger 1.01 Change date/time/attributes of multiple files. ChromeCacheView 1.22 Chrome Browser Cache Viewer ChromePass 1.05 Password recovery tool for Google Chrome Web browser. CleanAfterMe 1.36 Clean files and Registry values in your system. Clipboardic 1.10 Small and simple clipboard manager. Content Advisor Password Remover 1.01 CurrPorts 1.81 Displays the list of all currently opened TCP/UDP ports on your computer. CurrProcess 1.13 Displays the list of all processes currently running on your system. CustomizeIE 1.01 Add/delete toolbar buttons and menu items in Internet Explorer. DeviceIOView 1.02 Watch the data transfer between a software or service and a device driver. DevManView 1.06 Alternative to the standard Device Manager of Windows. Dialupass 3.05 Recovers Dial-Up passwords in all versions of Windows. DiskCountersView 1.00 Show disk drive read/write counters. DiskSmartView 1.02 Retrieves S.M.A.R.T information from IDE/SATA disks. DLL Export Viewer 1.36 Lists DLL exported functions and their memory addresses - for debugging. DNSDataView 1.05 Retrieve the DNS records (MX, NS, A, SOA) of the specified domains. DotNetResourcesExtract 1.0.1.0 Extract embedded resources from .NET applications. DownTester 1.20 Test your Internet download speed. DriverView 1.21 Displays the list of all device drivers currently loaded on your system. FastResolver 1.22 Resolves multiple host names into IP addresses/MAC Addresses and vice versa. FavoritesView 1.25 displays the list of all your Favorties/bookmarks in a single page. FileTypesMan 1.57 Alternative to the 'File Types' manager of Windows. FlashCookiesView 1.10 View Flash cookies stored in your computer. GDIView 1.05 Displays the list of GDI handles opened by every process HashMyFiles 1.67 Calculate the MD5/SHA1 hashes of your files HeapMemView 1.02 View the content of all memory blocks allocated in the heap. HTMLAsText 1.11 Converts HTML documents to simple text files. HtmlDocEdit 1.02 Simple HTML designer/editor IconsExtract 1.46 Extract icons and cursors from executbale files (EXE, DLL, OCX, CPL, etc.) IECacheView 1.32 List all files currently stored in the cache of Internet Explorer. IECookiesView 1.74 Displays the cookies that Internet Explorer stores on your computer IEDesignMode 1.00 Switch the active Internet Explorer window to design mode. IEHistoryView 1.45 Displays the list of all Web sites that you recently visited. IE PassView 1.17 Recover passwords stored by Internet Explorer (Versions 4.0 - 8.0) InsideClipboard 1.11 Displays the content of all formats stored in the clipboard. InstalledCodec 1.15 List Codec drivers and DirectShow filters installed on your system. IPInfoOffline 1.16 view country information about IP addresses. IPNetInfo 1.21 Easily find all available information about IP address. LiveContactsView 1.06 View the details of all contacts in your Windows Live Messenger. LSASecretsDump 1.21 Dump the LSA secrets from the Registry. LSASecretsView 1.21 displays the list of all LSA secrets stored in the Registry on your computer. MACAddressView 1.12 MAC address lookup tool Mail PassView 1.55 Recovers email passwords MonitorInfoView 1.05 displays essential information about your monitor. MozillaCacheView 1.27 List all files currently stored in the cache of Firefox/Mozilla browser. MozillaHistoryView 1.25 Displays the list of visited Web sites in Firefox/Mozilla/Netscape Web browsers. MessenPass 1.30 Recovers the passwords of instant messenger programs MUICacheView 1.01 Edit/delete MUICache items in your system MetarWeather 1.63 Decode METAR weather reports, and display them in a simple weather report table. MyEventViewer 1.36 MyEventViewer is a simple alternative to the standard event viewer of Windows. MyLastSearch 1.44 View your latest searches with Google, Yahoo, and MSN MyUninstaller 1.65 Alternative utility to the standard Add/Remove applet of Windows. MozillaCookiesView 1.30 alternative to the standard 'Cookie Manager' provided by Netscape and Mozilla. Network Password Recovery 1.24 Recover network passwords on Windows XP/2003/Vista. NetResView 1.16 displays the list of all network resources on your LAN. NetRouteView 1.05 GUI alternative to the standard route utility of Windows. NirCmd 2.41 Do many useful tasks from command-line. NK2Edit 1.06 Full NK2 (AutoComplete) editor for Microsoft Outlook NK2View 1.43 View the content of Outlook AutoComplete .NK2 file. NTFSLinksView 1.00 View the list of NTFS symbolic links/junctions in selected folder. OfficeIns 1.05 displays the details of all installed Microsoft Office add-ins on your computer. OpenedFilesView 1.46 Displays the list of all opened files on your system. OpenWithView 1.11 Disable/enable items in the 'Open With' dialog-box of Windows. OperaCacheView 1.37 Cache viewer for Opera Web browser. OperaPassView 1.01 Password recovery tool for Opera Web browser. OutlookAttachView 1.12 Extract multiple attachments from Outlook. OutlookStatView 1.06 Display a general statistics of your Outlook emails. PasswordFox 1.20 View passwords stored in Firefox Web browser. PCAnywhere PassView 1.12 PingInfoView 1.25 ping multiple host names and IP addresses. ProcessActivityView 1.11 Show the file activity for selected process. ProduKey 1.40 Displays the CD-Keys of MS-Office/Windows installed on your computer. PstPassword 1.12 Recover lost password of Outlook PST file. Remote Desktop PassView 1.01 Reveals the password stored by Microsoft Remote Desktop utility. RecentFilesView 1.10 Display the list of recently opened files RegDllView 1.40 RegDllView is a small utility that displays the list of all registered files. RegFromApp 1.21 Creates .reg file according to Registry changes made by application. RegScanner 1.82 Scan and find values in the Registry ResourcesExtract 1.15 Extract resources from dll/ocx/exe files. RouterPassView 1.00 Recover passwords from router config file. RunAsDate 1.10 Run a program with the specified date. SearchFilterView 1.00 view the search filters installed on your system. SearchMyFiles 1.47 Alternative to the standard "Search For Files And Folders" module of Windows. SeqDownload 1.25 Download sequence of images from the Web, and create animation from them. ServiWin 1.40 displays the list of installed drivers and services on your system. ShellBagsView 1.06 Displays the list of all folder settings saved by Windows. ShellMenuNew 1.01 Disable/Enable items in the New submenu of Explorer. ShellExView 1.47 Displays the details of shell extensions installed on your computer. ShortcutsMan 1.05 Lists all shortcuts on your desktop/start menu. ShellMenuView 1.12 Disable/enable static menu items in cotext menu of Explorer. SiteShoter 1.38 Save a screenshot of any Web page into a file. SkypeLogView 1.12 View log files created by Skype SmartSniff 1.60 Captures TCP/IP packets and view the captured data as sequence of conversations. SniffPass 1.10 capture the passwords that pass through your network adapter. SocketSniff 1.07 Watch the Windows Sockets (WinSock) activity of the selected process. SpecialFoldersView 1.13 Easily jump to special folders in your system. SysExporter 1.51 Grab the data stored in list-views, tree-views, list boxes, and combo boxes. URLProtocolView 1.15 View/disable/enable the URL protocols installed on your system USBDeview 1.67 Lists all installed USB devices that you previously used. UserAssistView 1.01 This utility decrypt and displays the list of all UserAssist entries UserProfilesView 1.01 View user profiles information on your system. VideoCacheView 1.61 Extract Web site video files from the cache of your Web browser VNCPassView 1.02 Recover the passwords stored by the VNC tool. Volumouse 1.72 Adjust the volume of your speaker with the wheel of your mouse. WebVideoCap 1.38 Capture Flash Video files and RTSP streams while watching them in a Web browser. WhatInStartup 1.20 disable/enable/delete programs that are loaded at Windows startup. WhoisCL 1.34 Get WHOIS information about a registered domain from command-line. WhoisThisDomain 1.41 Get information about a registered domain from WHOIS server. WhosIP 1.05 find all available information about an IP address from command-line. WinFontsView 1.05 Display sample of all fonts installed on your system. WinLister 1.13 This utility displays the list of opened windows on your system. WinPrefetchView 1.05 View the Prefetch files (.pf) stored in your system. WirelessKeyView 1.34 recovers lost wireless network keys (WEP/WPA) stored in your computer. WirelessNetConsole 1.00 View wireless networks information (console application) WirelessNetView 1.26 Monitor the activity of wireless networks around you. WinUpdatesList 1.23 Displays the list of all Windows updates (Service Packs and Hotfixes). OS: Windows NT/2000/XP/2003/Vista/7 Язык/Language: English/Русский (языковой пакет) Разработчик: www.nirsoft.net Размер: 16.59 MB


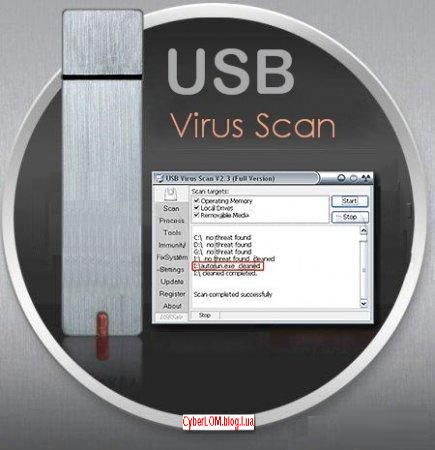
USB Virus Scan - это антивирусная программа для защиты компьтера от угроз, распространяющихся через съемные носители. По заявлению разработчиков, USB Virus Scan обеспечивает 100% защиту от вредоносных программ, заражающих съемные носители, такие как флеш-диски, флеш-карты, цифровые камеры, iPod, портативные медиа-плееры и т.д. После присоединения устройства к компьютеру программа автоматически сканирует его, блокирует и удаляет вирусы. Решает проблему с невозможностью открыть диск двойным щелчком в Проводнике Windows. USB Virus Scan также способна удалять остатки вируса с носителя, которые не были удалены другими антивирусными программами. Например, удаляет файлы autorun.inf, которые оставляет за собой вирус W32.Downloader и ему подобные. USB Virus Scan имеет небольшой размер, позволяет быстро сканировать съемные диски и не требует регулярных обновлений файла сигнатур. Год выпуска: 2009 Платформа: Windows® 2000/XP/2003/Vista Разработчик: http://www.usbvirus.com/ Язык: Английский /Русский Размер 1.2 Mb

